In fact, in February, the magazine announced that readers using ad blockers would be barred from accessing content unless they accept that Salon uses their computer to undermine the Monero cryto-coin.
Those who question the profitability of such an initiative are on the wrong track. The underlying business purpose is not to unwittingly turn visitors into virtual gold diggers, but to discourage them from using ad blocking software.
There is no better way than diverting devices from visitors to mine currencies like Monero or Bitcoin. The creation of crypto-currencies can seriously compromise the user experience: it reduces the speed and efficiency of the devices, even damaging the equipment. Added to that are the costs. In fact, the electricity costs of the Monero mining often exceed the value of the currency itself.
The most worrying is to see these unwanted entities getting into systems and devices via existing vulnerabilities or backdoors. Hackers are likely to exploit these systemic loopholes to steal personal data or sensitive business data, infiltrate networks for the purpose of installing ransomware and botnets, or simply resell their access and control to the vast network of cybercriminals raging on the Dark Web. For their part, the victims will find themselves plunged into an abyss of perplexity, wondering why their machine takes a long time to accomplish the simplest tasks.
Stalking the pirates
If it turns out to be increasingly lucrative, the diversion of users devices to undermine cryptocurrencies is not without casualties. In recent months, companies as diverse as Tesla, YouTube and a host of government agencies, including the British Public Health Service (NHS), have been victims of cryptocurrency mining malware.
Despite the fall in the value of Bitcoin, the scourge of "cryptojacking" marks no respite. The volatility of these virtual currencies and the ease with which anyone can divert devices from unsuspecting users make this technique particularly attractive to criminals: all they have to do is wait, collect money from money from thousands of machines controlled by bots, then cash their winnings when the value of the currency starts to rise.
The phenomenon needs to be monitored very closely as the detection of cryptocurrency mining often brings other even more serious security threats. Over the last six months, we have identified through the use of artificial intelligence (AI) and machine learning incident detection and response techniques, an upsurge in cryptocurrency mining on business, closely correlated with the price of Bitcoin. Customers could be warned in real time of a number of hidden hacks whose sole purpose was to take control of the machines, in the form of targeted or opportunistic attacks, to undermine Bitcoins and other crypto-currencies.
As part of our research, we found that some sectors, such as education and health, were particularly vulnerable to cryptojacking. These attacks are spreading around the world, with a higher detection rate of Bitcoins mining in rich and developed countries like the United States, the United Kingdom, Switzerland, Germany, Singapore and Japan.
Hit back
Why are these criminals allowed to act with impunity, diverting devices at leisure without being detected?
In the asymmetric world of cybersecurity professionals and cybercriminals, it is often the latter who take over, because they only need a single flaw to break into your business and carry out their illegal activities. Today, hackers generally have the advantage as most companies continue to concentrate the majority of their cyber security resources on perimeter defense.
Any attempt to intercept hackers who have crossed the perimeter defenses is often doomed to failure because criminals are masters in the art of disguising malware, for example by imitating signatures of known threats.
To combat the crypto-currency "miners", and any other form of malware and persistent advanced threat (APT), one must start by targeting their persistent limitation. Although malware is able to thwart the perimeter defenses by replicating benign traffic, once in the network, they behave predictably to perform their tasks. For example, they communicate via mining protocols or use remote command and control (C2) orchestration signals to and from the mining botnet member.
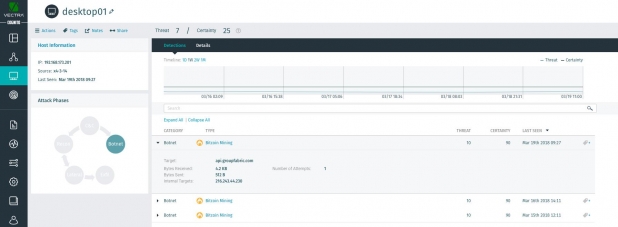
Vectra Cognito detects multiple instances of Bitcoins mining on an internal host.
These patterns of behavior are the main weakness of the attackers. A company that can immediately spot these warning signs can isolate and eradicate these attacks before they cause damage. In this respect, a manual solution, which would require many hours and days of work, would be much too slow to be effective and would not cover the entire corporate network.
This is where AI and automation have an important role to play. By leveraging the power of these technologies, the latest enterprise threat detection and response systems can detect entities whose behavior indicates malicious maneuvers within the network. The other benefit of this new generation of security systems is that they eliminate the influx of security alerts generated by traditional signature-based intrusion prevention and detection systems (IDPS), with most these alerts are false positives that are a waste of time.
In contrast, the new AI-based threat detection and response systems and machine learning deployed in the enterprise act as multiple "trigger wires". They instantly alert system administrators to the presence of unwanted visitors and provide information to identify behaviors that malware can not hide. We know from experience that the use of AI to analyze an attacker's behavior divides response times approximately 30 times compared to traditional alerts and intrusion detection methods.
Mining crypto-currencies is not in itself the worst thing that a company has to undergo. But the fact that hackers can access corporate networks, hijack devices and control them with such ease and for so long without being detected shows that a company does not control its own security. And that is a much bigger risk.
It's time for every company to respond to botnets that siphon their processing power and inflate their electricity bills, causing serious harm and exposing them to enormous risks.

